In this article, I will describe the various mobile access services we encounter under the same label. This article focuses on systems that can be used in commercial buildings with different door types. I have categorized them into four groups:
- Conventional Wireless Access.
- Mobile IDs or credentials (Virtual Access Cards).
- Stand-alone Mobile Access (Offline).
- Mobile ID and Stand Alone Mobile Access in the same application.
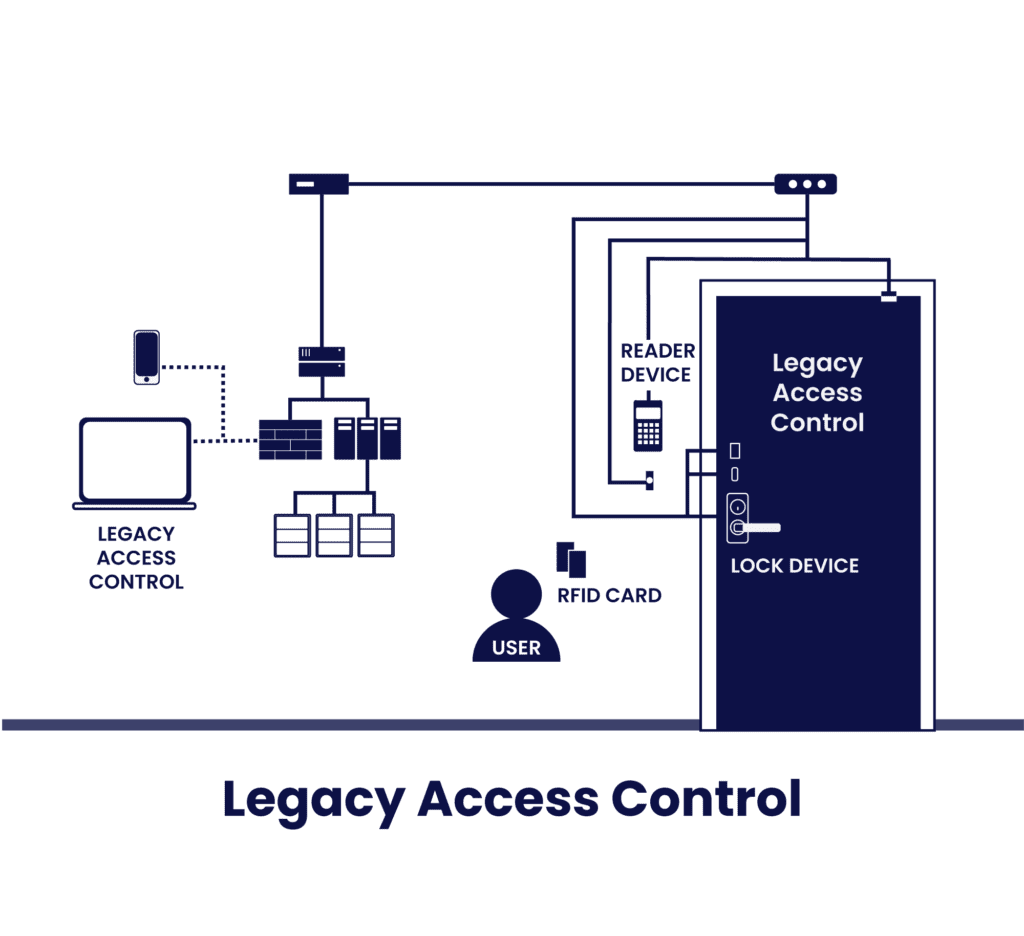
As a starting point, here is a graph of the conventional, legacy access control system. Traditional access control systems use NFC cards (RF ID) and key fobs. There are many different card technologies available with varying features of security. However, managing cards can be cumbersome, as they need to be physically delivered to the end user. Therefore, NFC cards and key fobs are not a practical solution for short accesses.
And now, let’s dive deep into Mobile Access!
1) Conventional Wireless Access: Mobile Access by using Online Connection to Access Control Services (wired or wireless)
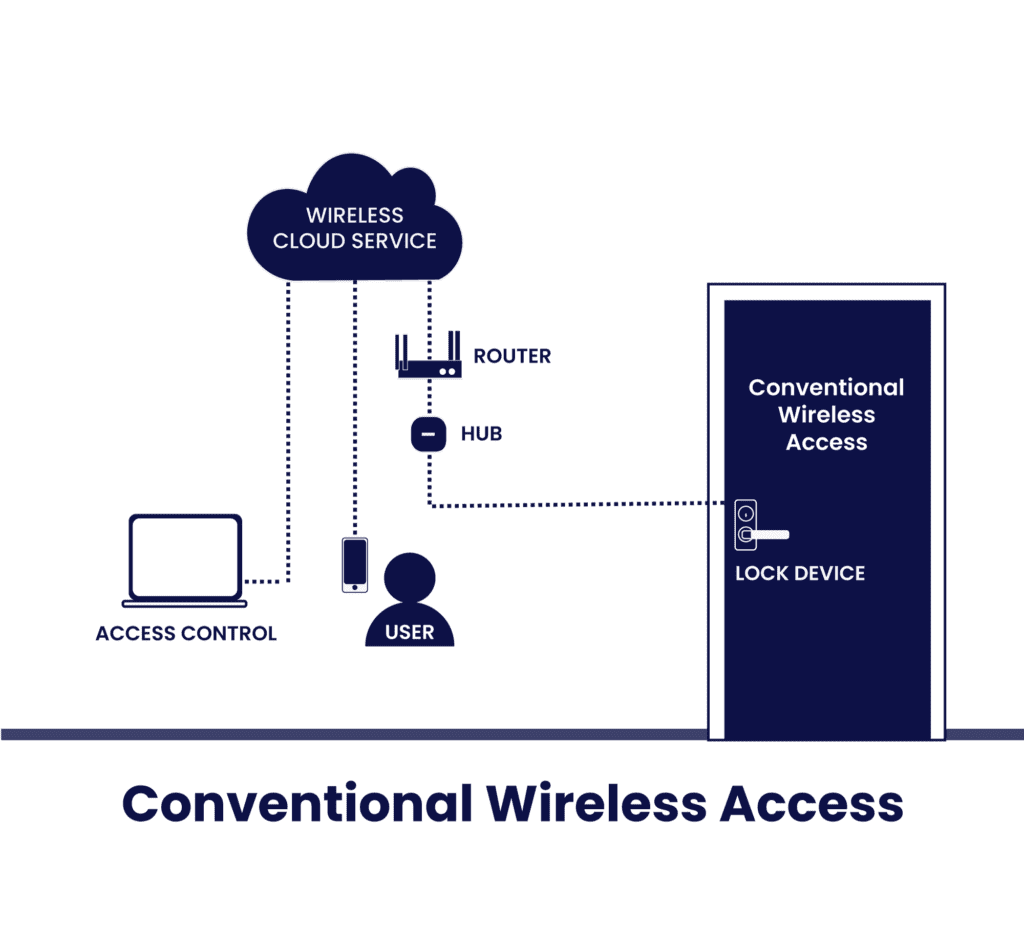
In this group, the mobile application connects to the cloud service and informs that the user wants to open a particular door. Then the system connects to the door to open it via either wired or wireless access control.
We call this group “conventional” because it does not differ too much from the traditional access control, except that it is connected.
That said, it has its pros:
+ Can be integrated into a reservation system.
+ Can be integrated into other mobile apps.
Nevertheless, the online character of the system has its downside:
– End users must have good Internet connectivity. Otherwise, latency ruins the user experience.
– It does not work offline, which limits its usage, for instance, in remote or underground places.
– Investment costs for the system can be high, especially for the wired system.
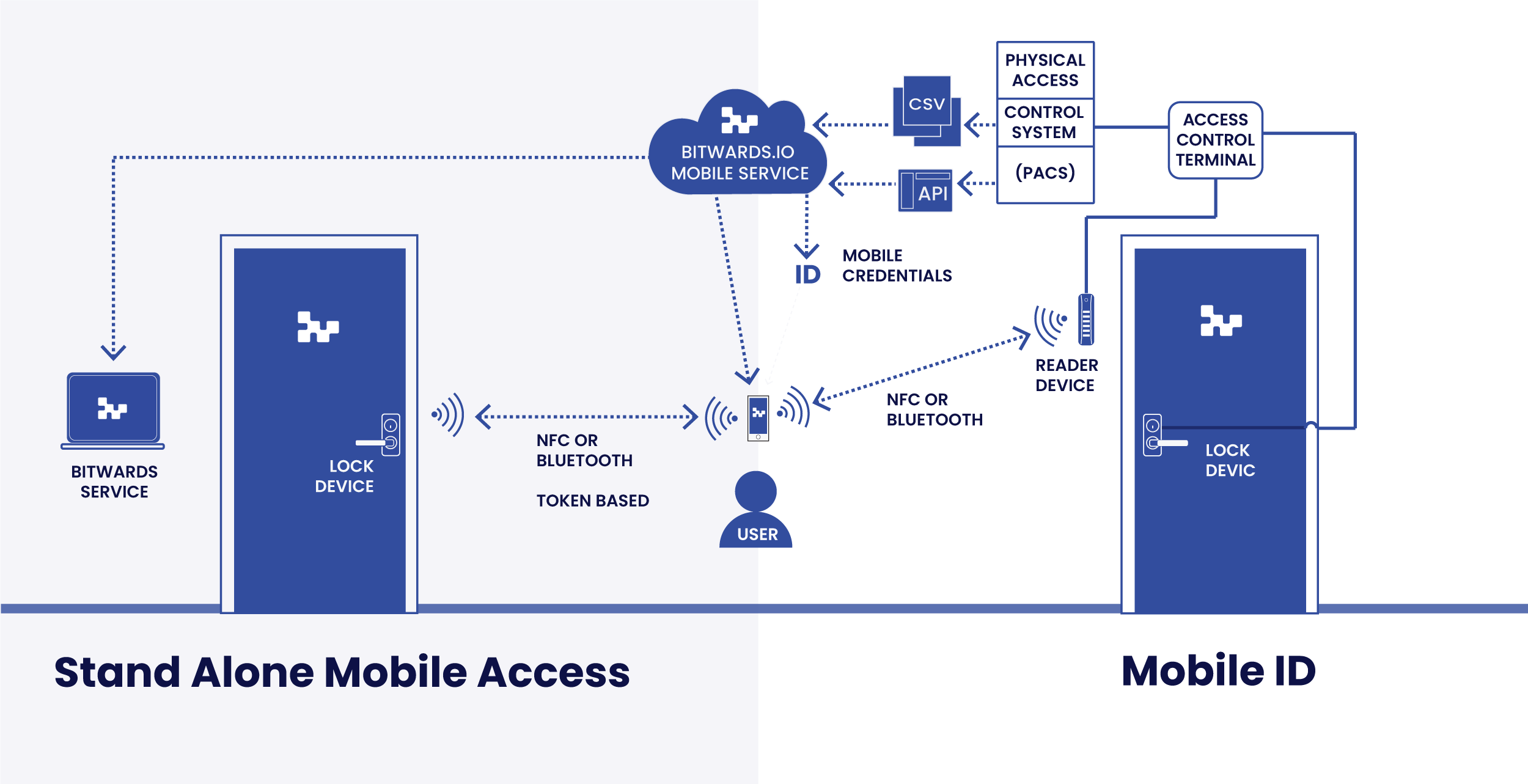
2) Mobile IDs or Credentials (Virtual Access Card)
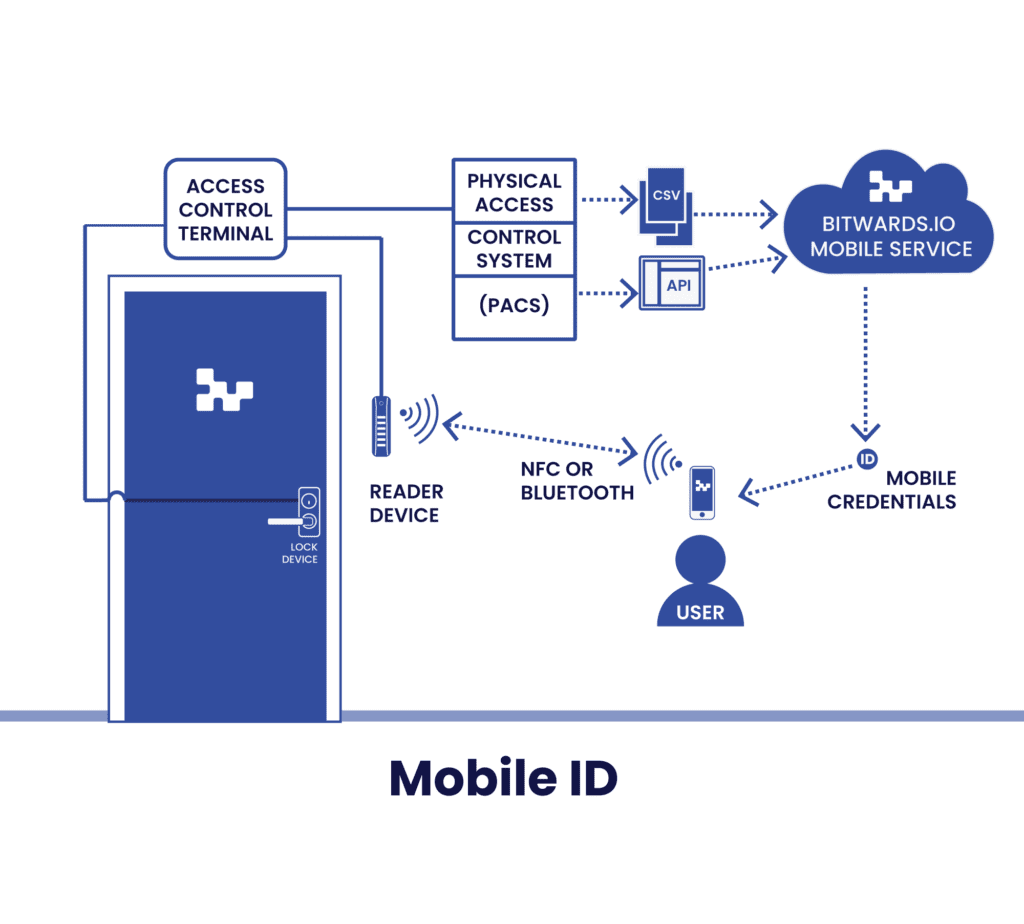
Bitwards Mobile ID belongs to this group
In this group of services, the mobile application acts as a virtual card, mimicking an RFID card’s behaviour. When the end users use the phone to identify themself either via NFC or BLE, the phone application will communicate with the access control reader.
The access control reader passes the received value over the Wiegand or RS-485 connection to the door terminal (or controller).
The access control system uses the user’s id to identify the person and verifies if the user’s access rights apply at that particular time. If the user has proper access rights, the access control door controller opens the door.
- In this model, the phone is a virtual credential card.
- It always requires wired or wireless access control.
- Typically access control system requires 5-10 minutes to deploy the changes in access rights to the door.
Pros and cons:
+ Enables retrofitting from old access control with the RFID only to mobile usage.
+ Can be used in parallel with RFID card.
– Investment cost for the system can be high, especially for the wired system.
– Not suitable to give access rights from the reservation system without integration into the access control system.
3) Stand Alone Mobile Access (Offline)
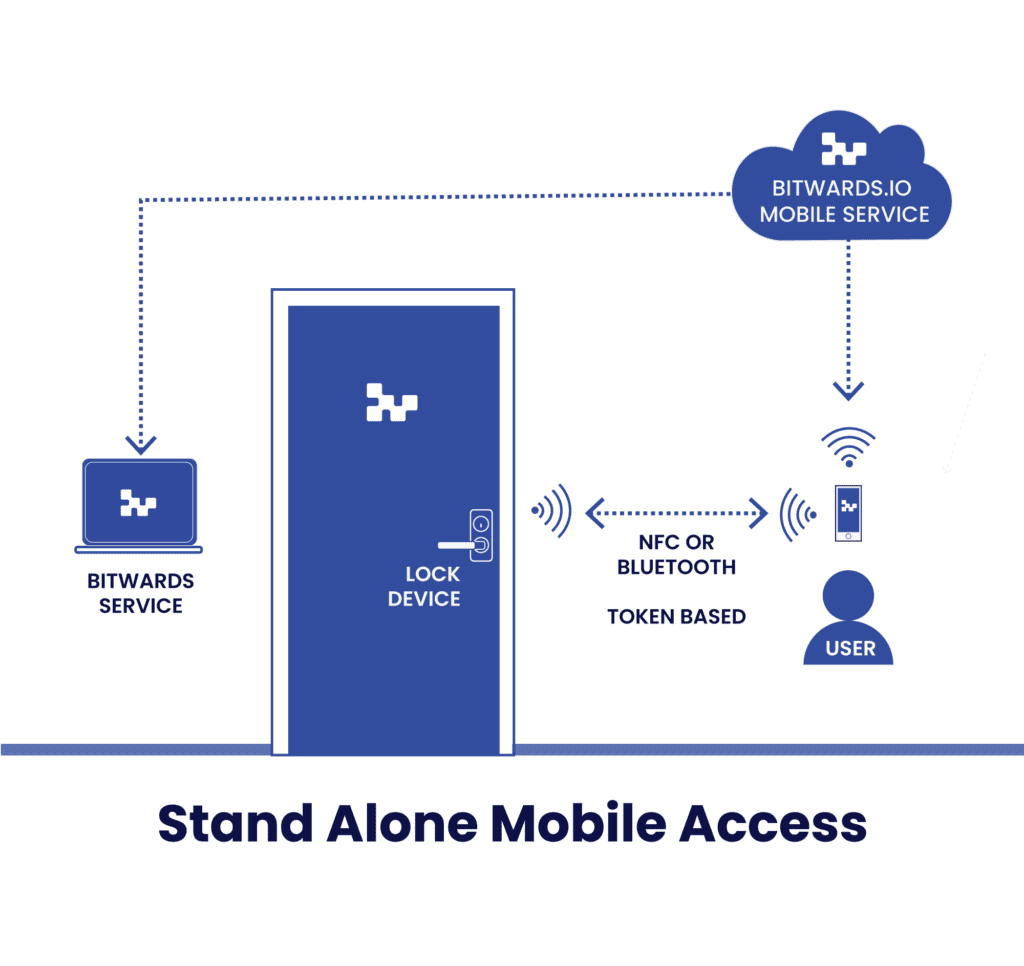
Bitwards Mobile Access belongs to this group
This group’s services are cloud services with access control and mobile identity management built in. In most cases, the cloud service issues the credentials to the mobile application.
When the user uses a phone application to open the door, the application communicates with the lock, providing encrypted data with checksums that the lock can use and deciding whether the end-user has access rights. The communication is carried out by using BLE or NFC and works offline.
The administrator uses cloud service to manage users’ access rights by utilizing door groups with weekly schedules if there are any. The service even adapts to include exceptions to the schedule.
The differentiator of the service over the traditional access control systems is that the service can instantly issue credentials to the end users. Shortly said, the APIs and the offline nature of the system enable fast admittance of the access rights over the API. End users can be sure that the door will open once the access rights are downloaded to the application.
Pros and cons:
+ It’s fast: instant access rights to the user through a mobile app in real time!
+ Investment costs are much lower than with conventional systems.
– Doors’ status cannot be monitored in real-time like with a conventional Access Control.
4) Mobile ID and Stand Alone Mobile Access in the same application
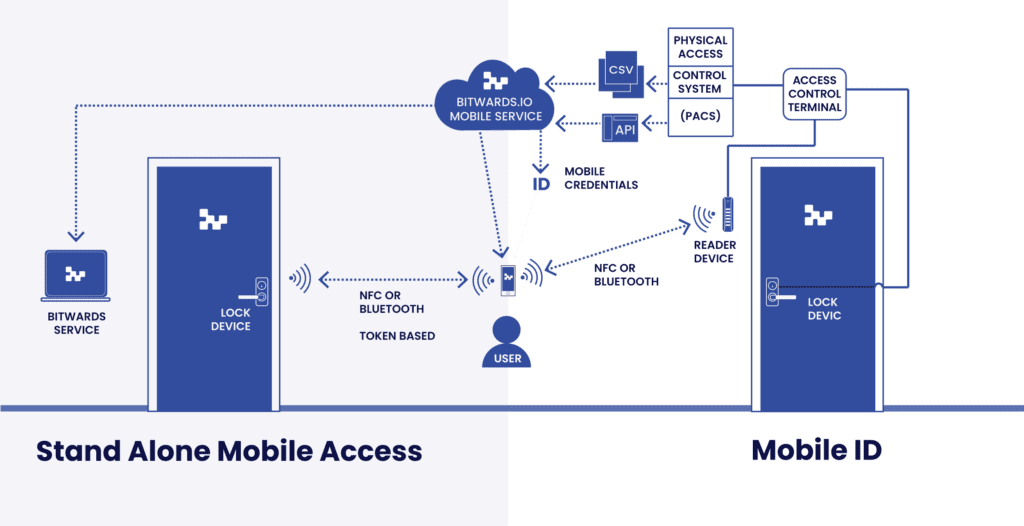
In this group, stand alone mobile access is combined with mobile ID. This means that the mobile ID service can be used where a traditional access control exists in parts of the building, typically in the entrance doors. Once inside, stand alone access can be used to access the parts of the building where traditional access control is not implemented.
However, the end user can still use one application to use the service with single sign in, meaning there is no need to change to logout and login to use different accounts. They can access all the doors and other access points of the building with one and only application.
- It enables retrofitting from old access control with the RFID only to mobile usage, and at the same time, it is possible to add new doors with lower investment costs.
- It offers modern APIs for the integration of new services.
- It is possible to utilize the existing investments in the door environment.
5 questions to ask about Mobile Access
The aim of this blog, with its graphic illustrations, was to help the reader understand that mobile access service groups vary.
To sum up, I want to leave you with these five questions you should ask yourself when evaluating which mobile access services you will employ:
- Do you need conventional access control, or would you instead consider a lighter, less expensive, more flexible solution that does not compromise security?
- Do you have existing access control and want to offer users the possibility to use a mobile app as a key, or do you want to implement a completely new system with mobile access possibilities? And how about a combination of the two?
- Does the service you are being offered work as an online service, or is it offline (stand-alone)?
- Do you need a mobile access system, or are you considering integrating it into a reservation system?
- How flexible is the system, considering your future plans?

Text: Niklas Kaustinen, CTO and Co-Founder, Bitwards
Graphics: Bitwards/Susanna Määttä