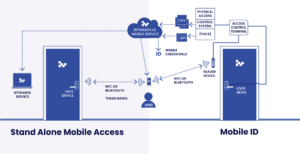
Is Apple entering the access control and security industry by offering mobile credentials so that users can access doors by using their iPhones?
In fact, Apple Wallet is not replacing access control. It offers a place to store your digital keys in secure storage of the phone. However, it still requires the conventional access control system to operate in the facilities and is only specific to Apple devices.
This article gives a basic overview of the role of what a Mobile ID actually is and the role of the Apple Wallet. In order to explain this, it is necessary to have a general understanding of how a conventional access control system works.
The Access Control System
The working principle of an access control system
The main elements of an access control system are:
- The server containing the access control software
- The door control panels
- Readers
- Electric locks
- Power supplies
- Cabling that connects the above components
- RFID credentials (cards, tags, or fobs)
A typical installation includes many other components as well making the overall system much more complex. The below diagram displays the basic configuration of an access control system.
Typical installation of an access control system. Diagram: Eljas Saastamoinen / BITWARDS
The basic operating principle is that the user’s credentials are stored and managed in the form of codes in the access control server and software. The system then delivers the credentials to the door control panels controlling the doors where the users need access. As users present their RFID credentials to the reader, it reads the credential and extracts the code, and passes it on to the door control panel. The door control panel then checks if the code exists in the database and based on the access control rules, it makes the decision to open the lock so the user may access it.
The user’s credentials and access rights are maintained on a whitelist which is maintained in the access control software. The whitelists are also delivered to the doors control panels so they can make local decisions on each user’s access. The control panels also periodically check for updates in the whitelist and thus need a constant connection to the server to retrieve the most recent list.
The Credentials
The credential represents a unique digital key – a code (usually a set of numbers like 3476132847) that is stored in the user’s physical credential. The credential is commonly in the form of a physical RFID card, tag, or key fob.
The key card contains a microchip and an antenna that is needed to communicate with the reader – mainly to transmit data stored (the credential) to the reader. The reader sends out electromagnetic waves that induce a current in the microchip’s antenna which powers the microchip so that the credential can be read and delivered to the reader when the user presents the card to the reader.
An encoder attached to the access control software is needed to program the credentials onto the key cards. The key card usually contains one unique credential which is matched with a user in the access control software.
To access a door, the user needs to present the key card to the reader. The reader then reads the credentials and passes this information to the door control panel. If the credential matches the credential on the whitelist, the door control panel will open the electric lock and the user can access it.
To protect the credential and maintain security in the communication, the credential is stored in an encrypted form on the key card. Also, specific encryption communication standards (like AES) are used during the wireless communication between the card and the reader to prevent disclosing the credential to others.
The encryption requires specific keys to be set in the reader and the key card. These must match in order to decrypt the credential in the reader before it is passed on to the door control panel.
The encryption keys are unique for each access control system which prevents the use of the same key card in others systems.
There are many RFID standards and technologies used for access control with Mifare developed by the NXP corporation probably one the most common technologies.
Mobile IDs
A short history of Mobile IDs
The evolution of Mobile IDs for access control is closely related to the development of contactless payments. Contactless payment refers to RFID technology used in credit cards and mobile phones.
Credit cards transformed from magnetic stripe technology to contactless payments quite late compared to RFID identification solutions used in access control. The first contactless payment was carried out only in 2004. The main reason for the late adoption was the lack of a proper standard. The introduction of the NFC (Near Field Communication) standard in 2004 was the awaited enabler offering the required security and specifications.
Since its birth, the NFC consortium initially formed by Nokia, Philips and Sony already had a focus on mobile payments. However, It was not until 2008 that the major credit card companies started the actual commercialization of the technology by rolling out credit cards with embedded NFC microchips. Contactless payment also required the payment terminals (the readers) to support the technology which led to the renewal of the payment terminals. This has been a massive task and only today, the NFC technology is the dominant standard in contactless payments (see the article: History of Mobile & Contactless Payment Systems).
NFC technology in mobile devices
With the roots of NFC technology in the mobile phone industry, the manufacturers started implementing the technology in mobile devices in 2010. Google introduced the Google Wallet and Android Pay in 2011 followed by Apple with Apple Pay in 2014.
The introduction of NFC in mobile phones was soon followed by the development of mobile IDs by numerous access control system manufacturers. New readers were introduced supporting NFC technology but the security of the credential stored on the mobile device was a concern and the first attempts to protect the credential were combined with the SIM card. This approach was however too complex and costly as it involved always the mobile operator.
The major breakthrough for Mobile IDs took place when Google released the so-called Host Card Emulation (HCE) in Android 4.4. This software architecture allowed the secure storing of the credentials in the deep hardware layers of the mobile phone eliminating the need for external security elements (like a SIM card or an external SD card) to store the credentials securely.
The HCE propelled the development of Mobile IDs but Apple limited the use of the HCE only to Apple Pay restricting the use of mobile IDs on iOS devices.
At the same time, Bluetooth Low Energy (BLE) technology was gaining ground rapidly in mobile devices and the developers of Mobile IDs quickly started the utilization of BLE as the dominant technology for Mobile IDs. The BLE offered a standard technology and more options and benefits also for iOS. The companies developing readers and mobile IDs for access control soon adopted BLE technology which has now become the dominant standard in the industry.
Mobile ID technology now and its limitations
Today, there are several reader manufacturers developing their own Mobile ID credentials. Each manufacturer has its own Mobile Application that supports its own readers.
The app communicates with the reader over BLE but Android phones can also communicate using NFC technology.
Mobile ID is used for identification at an access control reader. Image: Sirkku Liukkonen / BITWARDS
In addition to the Mobile IDs being manufacturer-specific, they are usually also unique for a single Access Control System prohibiting the interoperability between access control systems and different readers. To solve these restrictions, Bitwards has developed an open technology offering any reader manufacturer the option to use the technology for free and to offer end-users a single app to access any access control system.
The Mobile ID service offered by the Bitwards Access Platform can be connected to any Access Control System and offers automatic sharing of Mobile IDs to the end-users. The end-users only need the mobile app on their phone and once they sign in to the app with their email and password, they are able to use the mobile ID at the readers.
The Apple Wallet
Apple has noticed the restrictions of using the NFC for Mobile IDs on iOS devices and has gradually opened up the NFC interface also to Access Control System manufacturers.
Apple has released tools that manufacturers can use for implementing the Mobile IDs to the Apple Wallet. This is a place to store the Mobile ID (credential) in the Apple Wallet’s secure environment and offers the NFC communication channel for the Mobile ID with the reader. The mobile IDs are specific to each manufacturer and Apple is not interfering with the specifics of the access control system and mobile ID.
Apple Wallet is a place to store your keys but it still requires a master system to control the access for the user. Apple Wallet stores the access credentials (mobile IDs) issued by the access control system manufacturers, removing the need for a physical card.
Just as mobile payments are becoming the mainstream payment method, the phone is also rapidly replacing physical keys and keycards for access control systems.
Text: Eljas Saastamoinen, CEO, Bitwards